
Meet security requirements more efficiently with Isora, the GRC Assessment Platform powered by collaboration
Understanding where your organization stands when it comes to cybersecurity is critical—not just so you can pinpoint areas where controls are lacking and improve them, but to comply with standards, laws, and regulations.
That’s why Information security risk assessment questionnaires are such a powerful tool and an important part of an organization’s overall information security risk management (ISRM) program. They help organizations assess and identify potential security risks related to data and information systems with carefully designed questions that can uncover vulnerabilities and determine the likelihood of a security incident.
But administering an information security risk assessment questionnaire isn’t always easy—especially if you’re unsure where to start.
This guide from SaltyCloud contains everything you need to know about conducting an information security risk assessment questionnaire at your organization, from the basics to beyond. With this information, your organization can not only begin its journey to information security risk assessment questionnaires but become a seasoned expert on the subject and master the process from start to finish.
Also called self-assessment questionnaires (SAQs), information security risk assessment questionnaires evaluate how information is managed, protected, and shared by employees and the systems in place at an organization. It asks about the practices, policies, and technologies used to protect data. The responses help organizations understand where they might be at risk of data breaches or other security threats.
By identifying these risks, organizations can take appropriate measures to strengthen their security, like improving policies, training staff, or updating technology. They’re an important part of an overall information security risk management (ISRM) program because they help organizations:
Also called security risks or IT security risks, information security risks are potential threats and vulnerabilities that could lead to unauthorized access, use, disclosure, disruption, modification, or destruction of information and information systems. These risks can come from various sources, including cyberattacks, data breaches, human error, system failures, or natural disasters.
Unfortunately, the impact of these risks can be significant. In fact, global cybercrime costs are expected to reach nearly $14 trillion by 2028—a figure exponentially larger than the damage inflicted by natural disasters in a year. That sum includes downtime, intellectual property theft, damage and destruction, stolen money, theft of personal and financial information, fraud, embezzlement, post-attack disruption to operations, forensic investigations, restoring/deleting hacked data and systems, and reputational damage.
Put simply, information security risks can negatively impact operations, finances, legal standing, and reputation by threatening the integrity, confidentiality, and availability of the data organizations rely on to function. Managing these risks typically involves identifying potential threats, assessing their likelihood and potential impact, and implementing measures to mitigate or eliminate them.
Before you can mitigate or eliminate information security risks, you must first identify them. There are several common methods to identify information security risks, each with a different approach to uncovering and understanding vulnerabilities.
SAQs are the most versatile method of identifying information security risks. Because organizations can ask customized questions covering a broad spectrum of security practices, they can easily pinpoint areas where controls are lacking. Typically, information security risk assessment questionnaires are based on a security framework like NIST 800-53, NIST CSF, or ISO27001, to name a few. They’re most commonly used for self-assessments ahead of a formal audit.
SAQs are particularly effective for uncovering nonobvious vulnerabilities and gaps, and their scalability makes it easy for employees to participate across departments, teams, or business units. That helps organizations identify trends and solve security problems collectively rather than in isolated silos—which can foster a stronger culture of information security. By encouraging a unified front to cybersecurity, organizations can integrate insights and solutions across departments and improve overall security measures.
For example, by creating a questionnaire based on a cybersecurity framework like NIST 800-53, organizations can identify specific controls they haven’t implemented and consider those gaps as potential risks.
This method involves speaking directly with staff members, IT professionals, and management to gather insights about security processes, policies, and concerns. These discussions may reveal hidden vulnerabilities, misunderstandings about security protocols, and areas where security measures are lacking. Interviewing different levels of an organization—from the C-suite to the IT department—can help organizations get a better view of their security landscape by highlighting discrepancies between what is officially documented and what employees practice daily.
However, while interviews provide in-depth insights, they also have limitations, like potential response bias or incomplete knowledge. Individuals may unintentionally provide incorrect information about security practices or be unwilling to admit to bypassing security protocols to avoid repercussions.
Also known as “pen testing,” penetration testing involves security experts attempting to exploit vulnerabilities in an organization’s systems and networks. This simulated attack helps identify weaknesses in security infrastructure before a real attack occurs. Penetration testers use various tools and techniques to challenge physical defenses, software systems, and employee behaviors to see how well the system can withstand an attack. The results from penetration testing provide valuable insights into how actual attacks could breach the system and allow organizations to strengthen defenses accordingly.
Although extremely useful for uncovering technical vulnerabilities, penetration testing is limited in scope to the scenarios and systems tested at the time of the test. It may not identify all potential security issues, particularly those related to human factors or future system updates. Plus, it can be disruptive and expensive, which makes it less suitable for frequent or routine assessments.
Whether performed internally by a team or externally by an audit firm, audits are more comprehensive than other evaluation methods. While they may use questionnaires or checklists, audits delve deeper, systematically verifying compliance with policies and regulations. They aim to identify vulnerabilities and improve security measures to ensure that the organization’s practices are effective and compliant.
While audits provide a detailed snapshot of an organization’s compliance at a specific moment in time, their periodic nature can limit them—they might miss issues that arise between audits. Plus, audits can be resource-intensive and disruptive to daily operations.
Many automated security compliance tools can simplify part of the risk management process, but it’s important to remember that these tools are not a panacea. Unfortunately, complexity increases significantly with scale, particularly in large organizations with multiple business units and disparate requirements.
It’s important to remember that there is no such thing as truly “automated security compliance.” Human oversight has been and always will be essential because real people are needed to make sure non-automated aspects of security are effectively implemented, monitored, and adjusted based on evolving threats and organizational changes.
Use the following checklist to conduct information security risk assessment questionnaires across departments and with confidence.
First and foremost, you must determine what it is that you’re trying to accomplish with an information security risk assessment questionnaire. Are you attempting to establish a security posture baseline or meet compliance with a regulation like HIPAA, GLBA, or CMMC?
Based on your answer, the next step is to decide who needs to participate. All business units? Or only those handling regulated data? Who else needs to be involved? Executives (like the CEO), data owners (like your HIPAA officer), unit heads (like the VP of Research), IT staff, or nontechnical employees? What are their responsibilities? Are they participating by providing insights, responsible for mitigation strategies, or something else?
Defining and documenting these decisions will be important for the rest of the process. That’s why choosing the right tool to organize this information is crucial. Spreadsheets might work for a while, but they will eventually become too complex to manage.
A GRC assessment platform like Isora makes it easy for organizations to define a hierarchy and assign roles and permissions. That way, you can quickly launch questionnaires and scale across one, dozens, or even hundreds of business units and teams across your organization—all in a single platform.
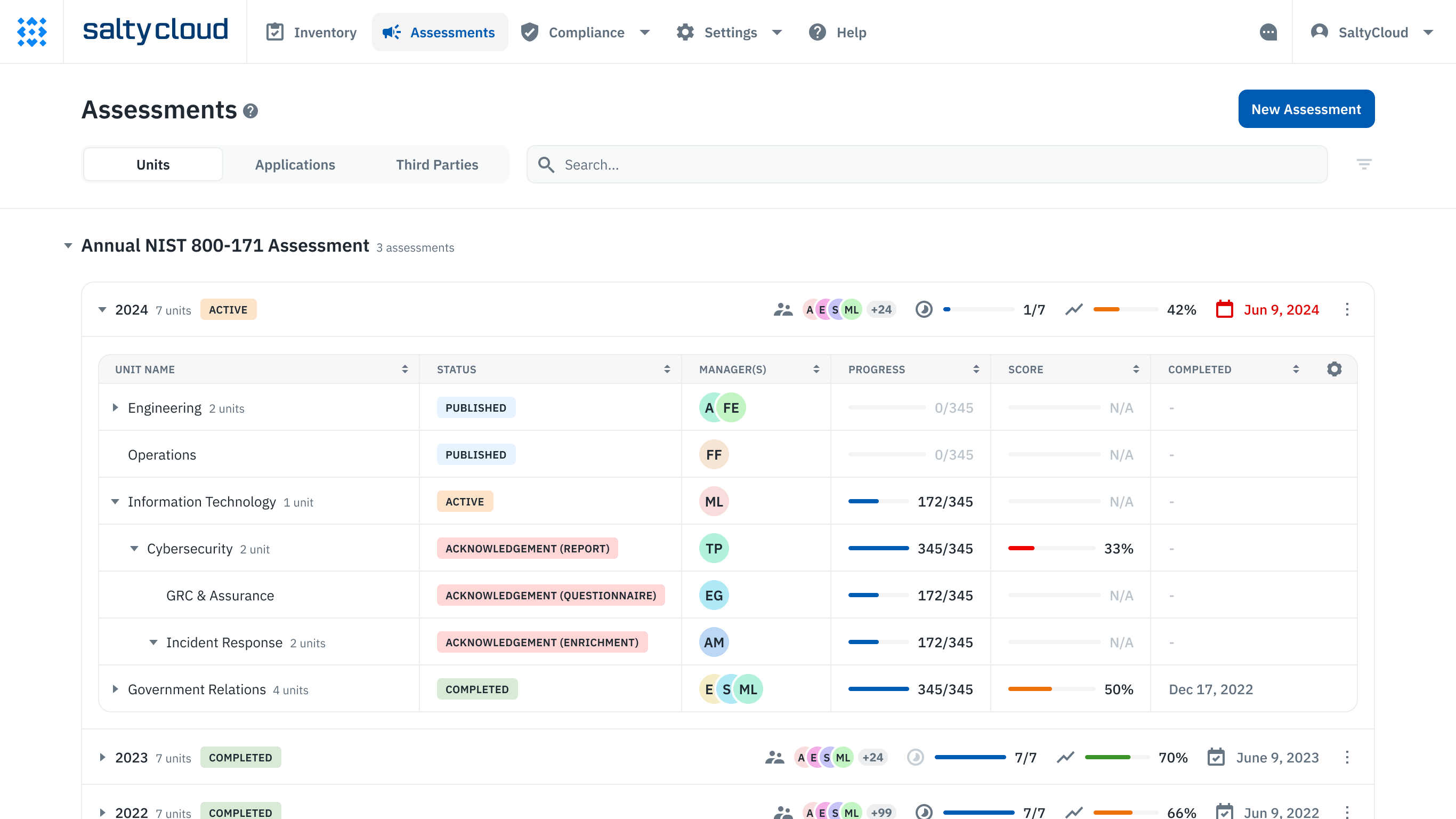
Information security risk assessment management on Isora GRC
Based on the scope determined during step one, choose an industry standard security framework to leverage that aligns with your requirements (e.g., NIST 800-53, NIST 800-171, NIST CSF, CIS, ISO27001, etc.) and create a questionnaire.
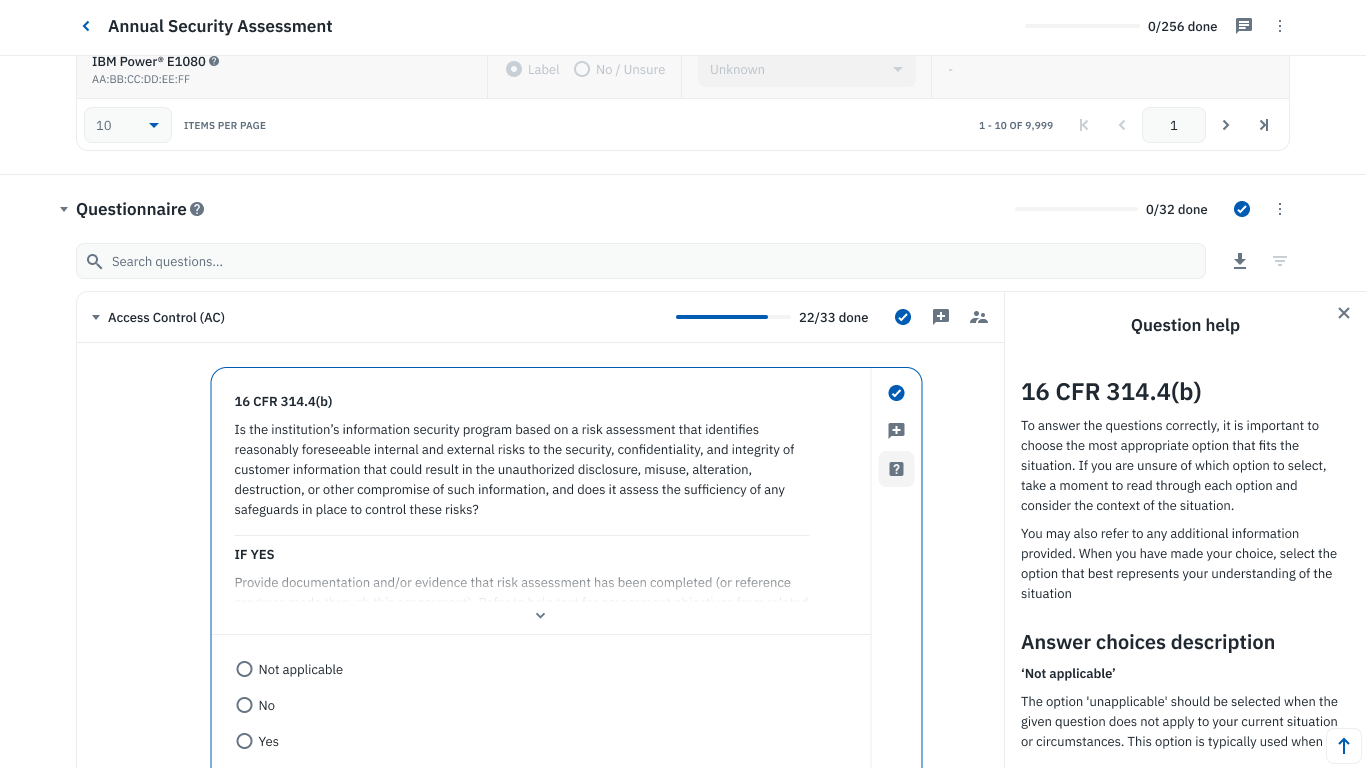
Remember that questionnaires can be used to collect qualitative and quantitative information, and questions can be multiple-choice, multi-select, or open-ended. Multiple choice responses can either be used to collect binary details like whether a specific security measure is implemented (Yes/No) or to measure maturity like when using Capability Maturity Model Integration (CMMI).
Consider the following example:
| Has the organization adopted secure secure development practices for in-house developed applications utilized for transmitting, accessing, or storing customer information including procedures for evaluating, assessing, or testing the security of externally developed applications utilized to transmit, access, or store customer information? | |
| Yes | Evidence Requirement: |
Please provide policy documents, process descriptions, or standard operating procedures that outline the mechanisms your organization has established. Include examples of industry-recognized cybersecurity and data privacy practices incorporated into your development lifecycle.
No matter how you approach it, creating an information security risk assessment questionnaire from scratch is no easy task. Even with a standard to guide you, you’ll need to design questions that are clear, actionable, and accurately reflect compliance requirements—a process that requires expertise and can be time-consuming.
A GRC Assessment Platform like Isora offers dozens of prebuilt questionnaires based on popular frameworks and regulations. It also makes it easy to create custom questionnaires or mix and match existing questions to design the best questionnaire for your organization’s needs.
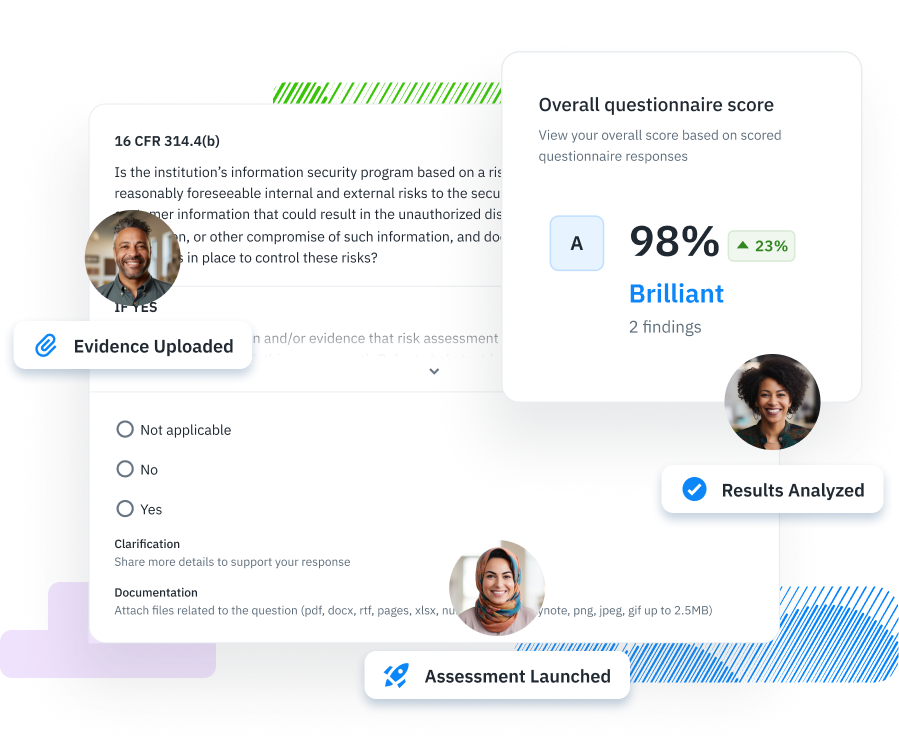
Collaborative questionnaire-based assessments in Isora GRC
Now it’s time to find the appropriate channels to distribute your questionnaire. Traditionally, this might be done via email.
But it’s unrealistic to simply send a questionnaire off and expect people to participate. First, you must get buy-in, which means putting effort into organizing a response. Ultimately, this process should align with your overall information security culture; everyone involved must be trained to participate.
Using a GRC Assessment Platform like Isora makes the whole process intuitive. It provides a central location where people across your organization with roles and permissions can access the questionnaire, provide responses, upload evidence, provide approvals, and review results.
Manage risk together Streamline your GRC assessmentsMeet security requirements more efficiently with Isora, the GRC Assessment Platform powered by collaboration

If you’re the information security professional tasked with managing the information security risk assessment questionnaire, you’ll be the point person in charge of going through the results, identifying gaps and trends, and communicating with people and teams across your organization. Depending on the scope and goals of the questionnaire, you’ll probably want to prioritize the findings by their level of importance and severity.
A GRC Assessment Platform like Isora automates the process, providing comprehensive questionnaire reports with highlights like letter grades, a breakdown by category, statistical measurements, and a risk matrix to help you identify high-risk and high-priority gaps.
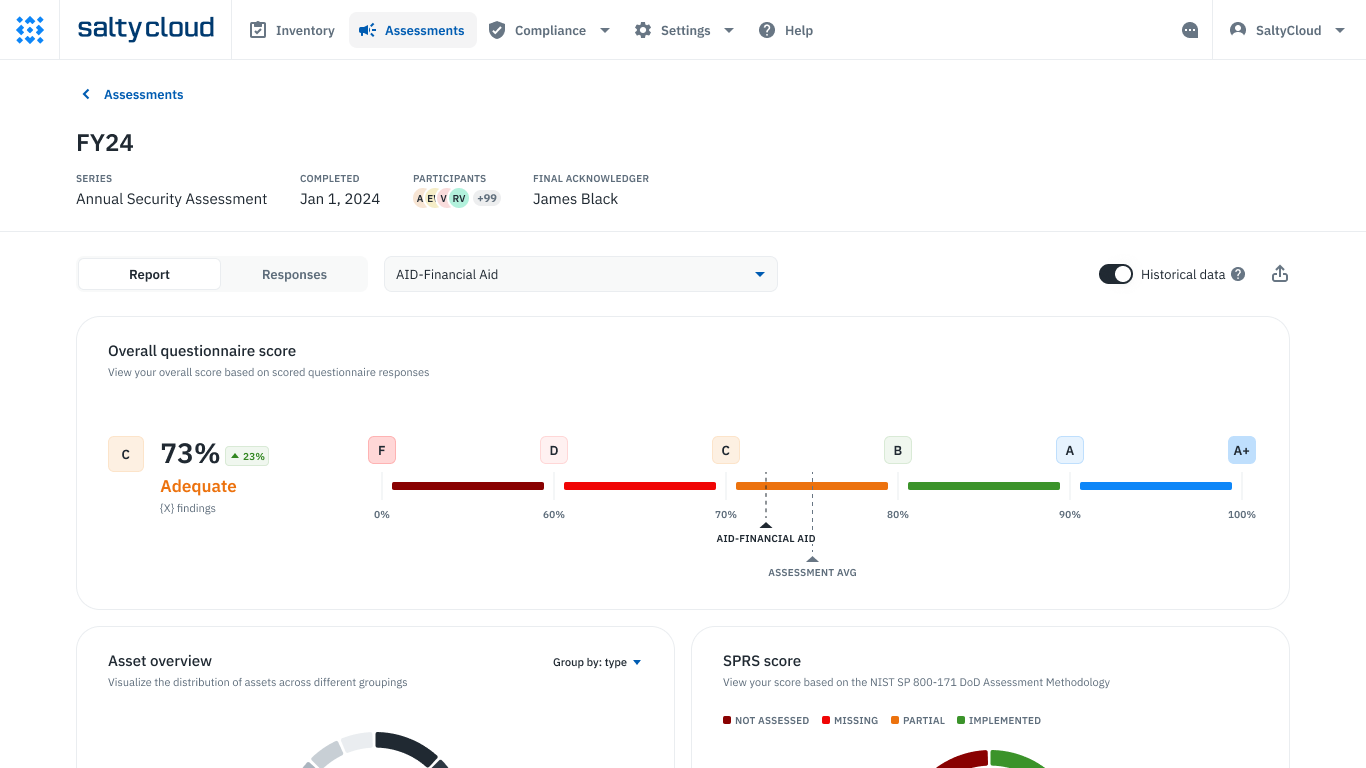
Assessment scorecards and reports in Isora GRC
An information security risk assessment questionnaire may have a start and a finish, but the process is never really over. Here are some things you should do once the results have been assessed:
By following these steps, organizations can ensure that they not only identify risks through questionnaires but also take concrete steps to manage them effectively over time.
Conducting an information security risk assessment questionnaire is a fundamental step toward strengthening your organization’s defenses against potential cyber threats and ensuring compliance with regulatory requirements. Now that we’ve walked you through the entire process—from the initial design of the questionnaire to the ongoing management of identified risks—you should be well prepared to launch an information security risk assessment questionnaire of your own.
But remember, effective information security risk management is not a one-time activity but a continuous cycle of assessment, action, and reassessment that’s part of a broader information security risk management (ISRM) program. Revisiting and refining risk assessment processes regularly not only helps your organization adapt to changes but also reinforces your commitment to protecting its assets and reputation. By diligently applying the practices outlined in this guide, your organization can achieve a high level of security preparedness and cyber resilience, turning information security risk management into a strategic advantage.
Manage risk together Streamline your GRC assessmentsMeet security requirements more efficiently with Isora, the GRC Assessment Platform powered by collaboration

Dive into our research-backed resources–from product one pagers and whitepapers, to webinars and more–and unlock the transformative potential of powerfully simple GRC.
Other Relevant ContentThis guide contains everything you need to know about conducting an information security risk assessment questionnaire at your organization.
Learn what self-assessment questionnaires (SAQs) are and why they're a valuable tool for your security risk assessments.
Dive into this Complete Guide for a comprehensive yet accessible pathway for developing an Information Security Risk Management program